The Okta Auth Manager Integration allows your app to authenticate users through Okta. This integration provides secure OAuth 2.0 / OIDC authentication and supports multi-tenant environments with customizable access policies.
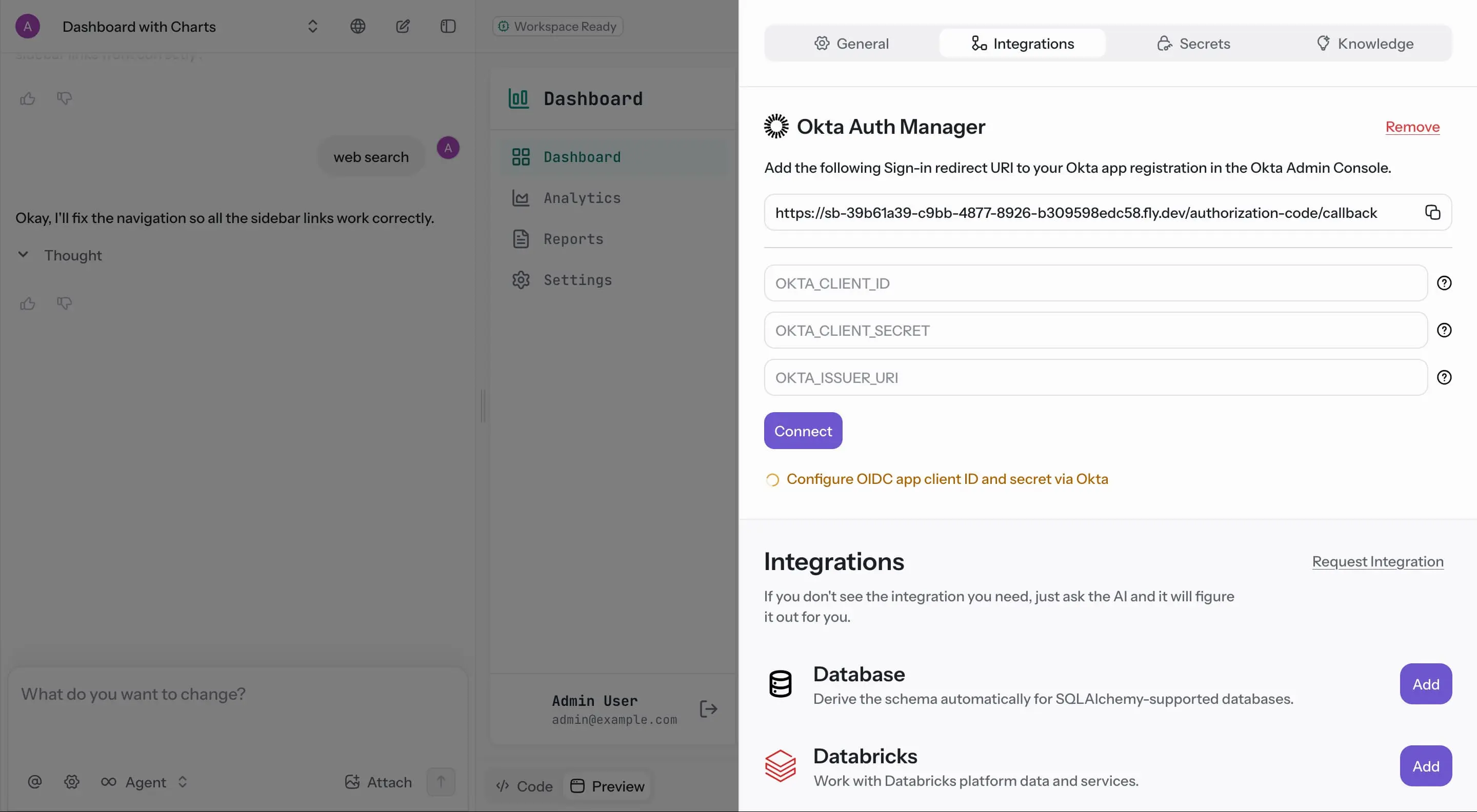
Before connecting, you need to create an OIDC application in the Okta Admin Console:
- Go to Okta Admin Console → Applications
- Click Create App Integration
- Select OIDC – OpenID Connect and choose Web Application
- Configure your app settings:
- Sign-in redirect URIs:
https://sb-39b61a39-c9bb-4877-8926-b309598edc58.fly.dev/authorization-code/callback - Assign to the correct Group or Everyone depending on your access control
- Sign-in redirect URIs:
- Save the app integration.
After creating your Okta app, collect the following information:
- OKTA_CLIENT_ID:
0oa1abcdXYZ2efGhI5d7Your app’s Client ID from the Okta Admin Console
- OKTA_CLIENT_SECRET:
xYzABC1234567DefghIJKLmnopQrstuVWYour app’s Client Secret (keep this secure)
- OKTA_ISSUER_URI:
https://dev-12345678.okta.com/oauth2/defaultThe Issuer URL from your app’s settings
Note: Always use separate Okta apps for dev, staging, and production environments to avoid mixing credentials.
- Go to the Integrations section in your app settings by clicking
@and then selecting the Integrations tab. - Click Add next to Okta Auth Manager.
- Fill in the credential fields:
- Enter your Okta Client ID
- Enter your Okta Client Secret
- Enter your Okta Issuer URI
- Click Connect to save the integration.
Your app can now authenticate users through Okta using the secure OAuth 2.0 / OIDC flow.